The Canada Emergency Response Benefit (CERB) is an essential part of the Canadian Federal Government response to the COVID-19 pandemic. With an estimated cost of over $71 billion dollars and limited vetting of applicants, the CERB program has been known to be vulnerable to fraud since launch. Since the program’s launch, media outlets have reported that between 200,000 and 3,000,000 erroneous or fraudulent claims have been made.
News reports now claim that malicious actors targeted the Canada Revenue Agency (CRA) accounts of over 5,500 Canadians. These malicious actors would have used credential stuffing attacks against the CRA. In this blog post, we investigate whether this could really be the case. We also provide hypotheses as to how this could have happened.
What are credential stuffing attacks?
The figure below explains how malicious actors launch credential stuffing attacks. These attacks take advantage of the fact that most people commonly reuse the same password across multiple websites. This means that if an individual’s username (or email) and password combination leaks online from a data breach, malicious actors can use that information to try and login into many different websites.

Automating credential stuffing attacks
The process of testing leaked credentials on different sites is known as credential stuffing attacks. It can be accelerated by using automated software. The video below was recorded by a malicious actor. It demonstrates how other actors like them import leaked credentials and automatically test them. In this case, the software targets a music streaming service. It finds 3 credentials (hits) that could be reused to login to that service in a matter of seconds.
Unique usernames as protection against credential stuffing attacks
Credential stuffing attacks are possible because most websites use emails as usernames. Another factor is that individuals also reuse the same password across multiple websites. With this and other reasons in mind, most financial institutions have opted not to use emails to identify their customers. This has protected them, to some extent, from credential stuffing attacks.
The CRA adopted a similar strategy and requires Canadians choose their own username when creating an account. In addition, Canadians must select a number of security questions and answer one of them every time they log in to CRA from a new computer.
This raises questions about the latest news reports that identify credential stuffing attacks as responsible for the account takeovers at CRA. How may malicious actors gain access to these accounts given the security measures put in place by the CRA?
Reusing usernames AND passwords
It is possible that malicious actors adopted a more sophisticated type of credential stuffing attack. Malicious actors may have extracted the first half of leaked email addresses — what comes before the @ — to test as a username. A Canadian with the email address [email protected] for example may also have used westcoastbuddy as their CRA username. If this person reused a password from another website on their CRA account, it is then possible for a malicious actor to take over their account. They could then ask for CERB payments.
Other methods used to takeover accounts of the CRA
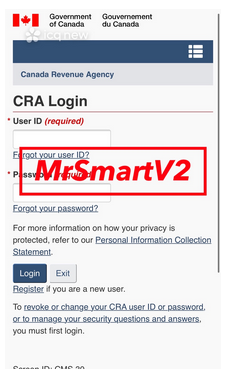
Our investigation shows that malicious actors may have used other techniques than credential stuffing attacks to target Canadians and the CRA. We have found some evidence that malicious actors could be using phishing techniques to gather CRA credentials. With a phishing attack, the victim is tricked into clicking on a link to a fake CRA page. On that page, they are asked to enter their credentials, as well as the answers to their security question. Such scampages are currently available for sale, and likely in use by malicious actors to gather credentials. The image below presents an example of such a page, that near-perfectly replicates the CRA user interface.
Conclusion
Our analysis shows that it is therefore possible for malicious actors to use credential stuffing attacks to target the CRA. The main limit to this type of attack is the need to answer at least one security question correctly when logging in. Malicious actors could source the answers to these questions in leaked databases of users that contain the answers to security questions from other websites, search in social media posts and pictures or even use technological solutions that bypass the need to answer security questions altogether.
The best solution to prevent attacks against CRA accounts is for individual Canadians to be vigilant, and to know the risks. By visiting their CRA account on a regular basis, Canadians can quickly detect if a malicious actor has changed their password or banking information, and notice other irregularities in their accounts. Canadians can then report these potential data breaches to the CRA.
As an added protection, credential stuffing attack prevention services can compare lists of leaked credentials found online to those used by individuals for their CRA accounts. Flare Systems is one of the few companies that can verify in real time the leaking of credential combination on the internet or the darkweb. Flare Systems flags those accounts as potentially vulnerable to credential stuffing attacks. For more information or for a demo, do not hesitate to contact [email protected].