The F.B.I. has just published its latest report on cybercrime complaints it received in 2020. The picture drawn should raise concerns for most CISOs, and unfortunately raises even more questions than providing answers. The main take-away from the report is that 791,790 cybercrime complaints were made in 2020. Those complaints were responsible for over US$4.2 billion in losses. This represents an almost 70% year-over-year increase.
COVID-19 related complaints dominate 2020
Without surprise, COVID-19 related complaints represented a significant share of all complaints reported to the F.B.I. These first relate to government program fraud where malicious actors submitted claims in the name of individuals and companies. In many cases, the victims found out about the fraud when they tried to apply for these same programs, but were rejected for having already applied. In a previous post we discussed that California estimated that up to 27% of its unemployment program for COVID-19 was spent on fraudsters.
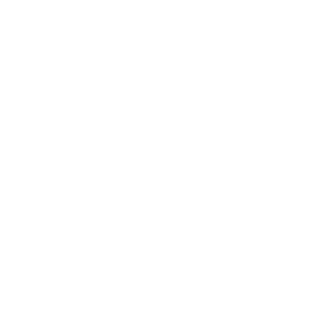
Another significant issue was the vaccine and other prescription fraud where malicious actors tricked people into purchasing worthless medicine, or paying for vaccines that did not exist. This includes a fake lottery for vaccines. We have witnessed such scams on forums and chat rooms, such as the message below that was posted on ICQ in February 2021.
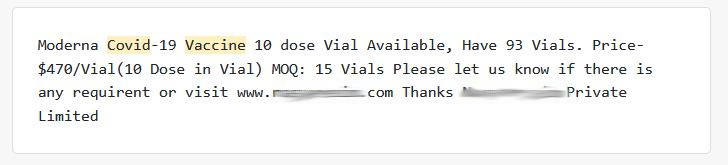
American Complaints, International Victims
Although the F.B.I. compiles complaints from U.S. individuals and companies, many of the victims listed are located in other countries. The map below shows the distribution of victims across the globe. Interestingly, Canada is the second country in terms of victims with over 5,000 victims. This number is far from the UK with 215,000 victims. The top victimized countries also include India, Greece and Australia.
Business Email Compromise As the Most Common Threat
The F.B.I. identifies 3 types of illicit activities that have become major issues:
- Business Email Compromise (BEC)
- Tech support fraud
- Ransomware
By all accounts, all of these activities have increased in number and sophistication. In the case of business email compromises, malicious actors now steal confidential information from emails such as tax forms and credentials to launch attacks against computer networks and partners of the companies.
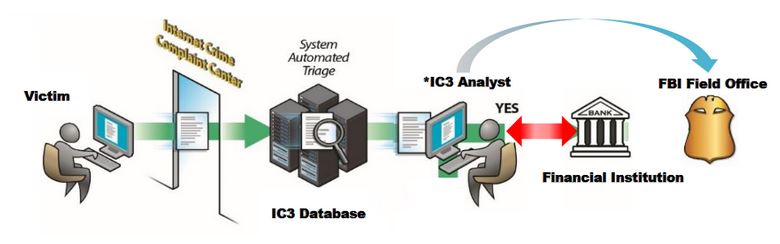
The F.B.I. has put in place a new team in 2018 to help recover funds that were stolen. This Recovery Asset Team is part of the Internet Crime Complaint Centre (IC3) and receives reports about stolen funds through attacks such as business email compromise. This team’s results are impressive, with over 80% success rate when contacted rapidly, and over USD$380 million in frozen funds from potentially fraudulent wire transfers.
Ransomware appears to receive few complaints based on the 2020 statistics. The disclosed losses are only for USD$29 million, a tiny fraction of other estimates of the impact of ransomware. Still, this figure is more than tripled from what it was the year before, which was also tripled from the year before that. This growth suggests that ransomware complaints will continue to grow exponentially over the coming year.
Disclosing Breaches to Law Enforcement
The latest statistics published by the F.B.I. draw a picture of the activities of malicious actors. This picture is however greatly distorted by the dark figure of crime. Law enforcement indeed only comes in contact with a small proportion of all crimes, either through complaints or through neighborhood watch. The share of crimes that are part of official statistics varies depending on the type of crime, with drug transactions having possibly one of the highest dark figures. Homicides are of course one of the types of crimes with the lowest dark figure.
While the numbers presented in the F.B.I. may seem important, they still only represent a partial view of all crimes that occurred in the past year. Moreover, these numbers do not take into account offenses reported at the lower levels of enforcement. This serves as a reminder of the importance for more comprehensive statistics on cybercrime, and the limits of using biased data to build prevention models.
A significant worry is the 70% increase in complaints year-over-year. 2020 could be a special year because of COVID-19, with victims having more time to report crimes to law enforcement because of their work-from-home setup. The more reasonable hypothesis however is that victims are becoming more familiar with the reporting process, and are starting to report more of their victimization events to law enforcement.
In the context of such a huge increase, the question then becomes if law enforcement agencies are investing in their cybercrime investigation at the same rate as complaints. With so many complaints to handle, law enforcement will need to hire significantly more investigators and civil employees to collect, analyse and investigate crime reports. There is no evidence at this point unfortunately that this is the case, leading to questions about the effectiveness of the response to cybercrime, and the close rate of cybercrime cases in the coming years. The problem here is not one of willingness on the part of the law enforcement agencies, but one that is political: will legislators increase the budgets for law enforcement agencies so that they can respond adequately to this growing threat?
Without an effective budget and response to cybercrime, the task to prevent and respond to cybercrime may fall more and more on the shoulders of individuals, but also of private companies that have the information and funds malicious actors seek to steal. There again, security budgets will need to be aligned with the growing threat of cybercrime. As for all problems, the question is not always of how much is spent, but rather how budget is spent, and for what purpose.
This is perhaps where digital risk protection (DRP) shines the most. It provides a comprehensive view of the external threat landscape and enables CISOs to allocate resources based on known external threats on their company, but also on their industry in general. Few malicious actors have the resources of a medium-sized company, let alone a large corporation. Malicious actors therefore play on the interstices in the security of companies. By understanding external threats, it is possible to plug those interstices before they lead to a costly data breach that damages your brand and reputation.