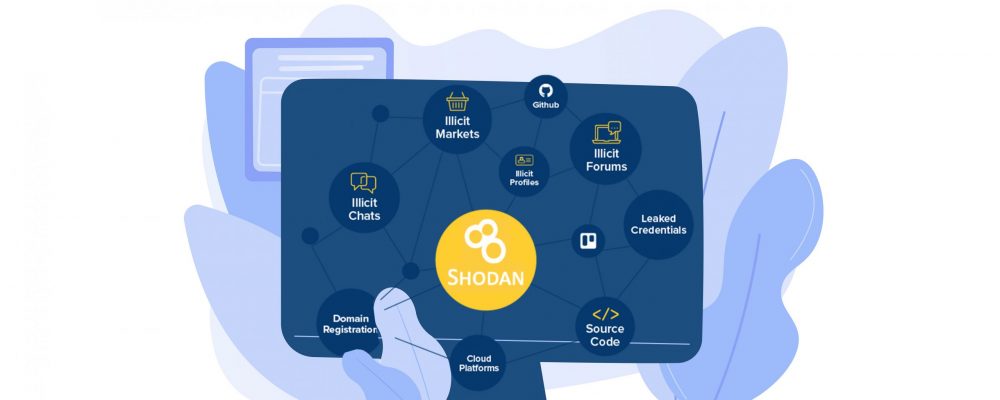
Monitoring open ports on Shodan can sound simple, but the reality is that there is a lot of data which regularly changes. Having yet another source that generates multiple alerts is not something many experts look forward to.
Alert Prioritization
There are two broad types of alerts that can come from monitoring Shodan: alerts about your own infrastructure, and alerts about unexpected hosts and shadow IT.
The findings, analysis and remediation steps are different for both use cases, and Firework uses a different approach for each of them.
Alerts for Known Infrastructure
For known infrastructure, searches are run by Firework on Shodan for any IP address, domain or subdomain that the platform knows about.
In this case, the objective for a platform like Firework is to identify unexpected or unusual events.
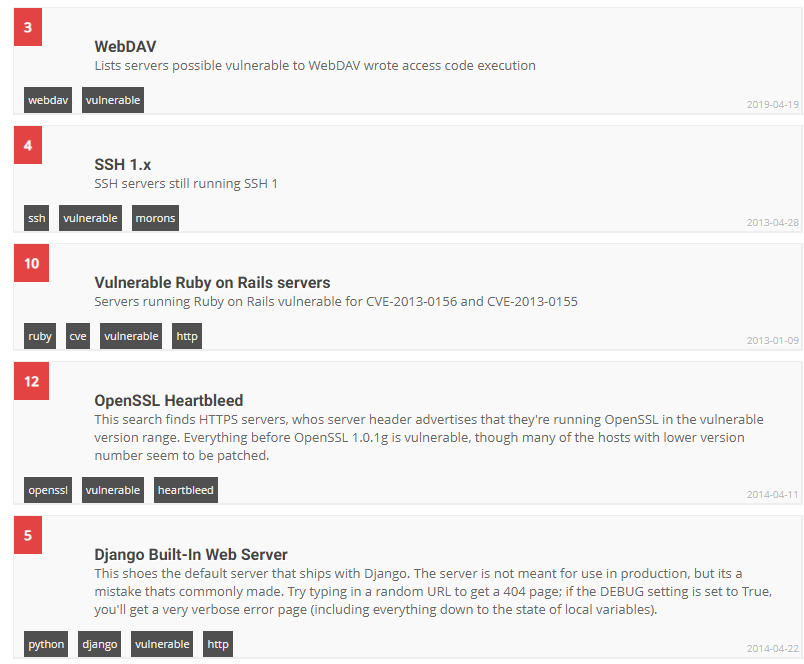
For example, it’s normal for port 443 to be open on the server hosting the main domain name of an organization. On the other hand, it’s unusual to have a port 9200 (Elasticsearch) open on a subdomain related to a QA team. It’s also a risk to have an open service with known vulnerabilities. Shodan actually enriches network responses with context based on version numbers and even enables searching by vulnerability, as the image below shows.
As a result, Firework uses a set of heuristics to evaluate the risk of a Shodan result and assign it a 1 to 5 score based on the system-wide rating system. This enables users to avoid alerts for false positives, and to quickly filter search results when doing an investigation or an assessment.
Alerts for Shadow IT
Servers sitting outside the known perimeter can also be used as an entrypoint for a malicious actor, and Shodan can help the actor identify these hosts.
In this case, the objective for Firework is to run searches based on domain names and keywords related to an organization to identify hosts that contain hints of any relation with the organization. Results found this way are also scored on a 1-5 scale.
Extract Value from Shodan
This prioritization approach allows organizations to take advantage of Shodan’s powerful scans and to quickly and continuously monitor what information is passively available to malicious actors, whilst keeping a focus on high-priority alerts.
To learn more about Firework and Shodan, book a demo with our team.
> Read previous article about “Shodan: Where OSINT meets port scanning”



