When a data breach occurs, most companies contact their customers by email to inform them of what happened, which information may have been compromised, and what the company is doing to minimize the negative impact.
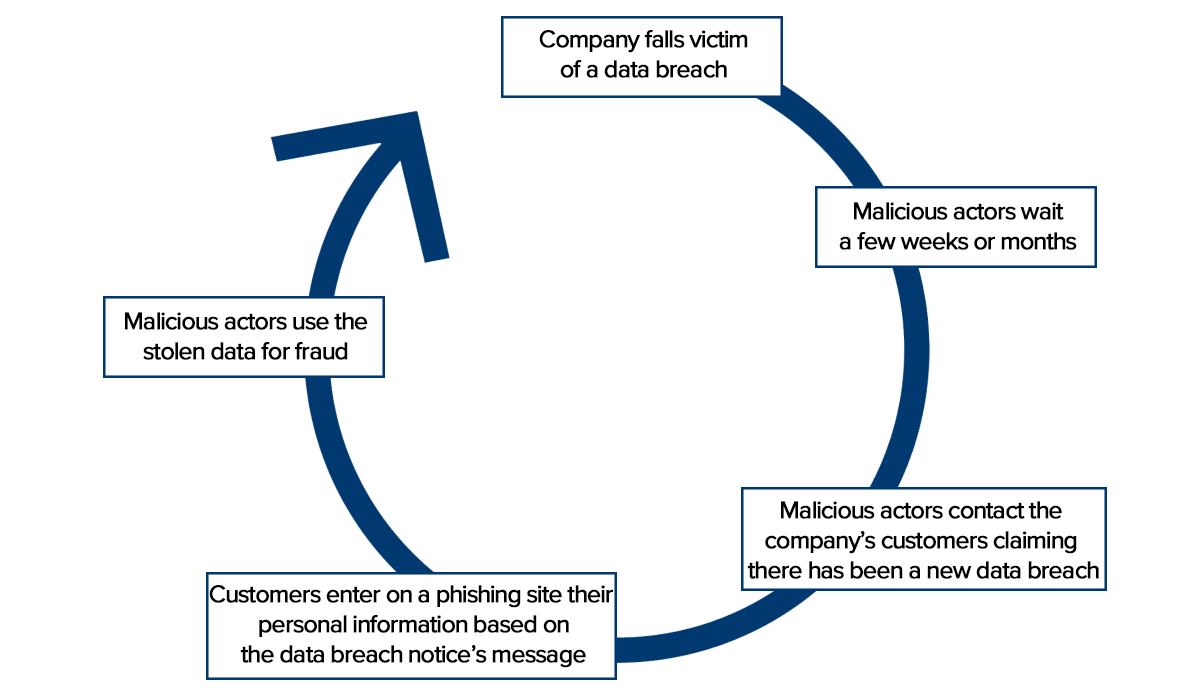
This is what happened in the summer of 2020 when malicious actors manipulated a website vulnerability to steal the personal information of about 10,000 customers of a cryptocurrency storage (wallet) company. The company reacted promptly and communicated the breach to its customers by email.
According to Bleeping Computer, three months later, customers started receiving another email claiming the company had fallen victim to yet another data breach. What made this email special was that there was no second data breach; it actually came from malicious actors trying to trick customers into clicking a link in the email. Officially, this link was supposed to help customers secure their cryptocurrency holdings; in reality, it led them to a phishing site where they were asked to provide malicious actors with everything they needed to steal their assets.
We present this strategy in the model below, which shows how one data breach can lead to another – and possibly more – data breaches.
Turning your own messages against you
What makes this strategy so effective is that customers are likely to believe a message they have seen before, for an event that has already happened.
This strategy is possible because malicious actors could copy the original data breach notice sent to customers. In this sense, the company, like many others, adopted a disclosure process based on what we call ‘cheap signals’.
Signals can be defined as communications, either written or visual. An email is a cheap signal in that it is easy to copy, and to send. A gang tattoo is also a signal that its wearer sends, to communicate to others that they are to be taken seriously. Because it can never be removed, a gang tattoo represents a signal that is much more costly to send. Members of the Japanese mafia – the Yakuza – take cost signaling to an even higher extreme, by amputating a part of their right pinky. Called Yubitsume, this signal has many connotations and reasons for still being around. One of them involves sending a clear and costly signal that you are willing to join the Yakuza. An undercover agent, or someone with a weak interest in the organization, is highly unlikely to go through Yubitsume. Only those willing to pay the price can and will become members of the Yakuza.
Preventing malicious actors from abusing your messages
What we can take-away from this case study is that signal costs do matter. Using cheap signals to communicate important information is a risky practice that can increase the number of attacks against your company.
The Yakuza lower their risks of arrests by only accepting in their ranks members that have paid a significant sacrifice. Few, if any, undercover agents are interested in joining their ranks to build a case against them.
A solution to prevent successful attacks is to increase the costs of the signals you send so malicious actors are unable to copy them. However, in today’s world of virtual communications, increasing signal costs is easier said than done.
Despite this, there are still a number of solutions you could implement in your enterprise :
- Send communications through the mail. Yes, sending a piece of mail is cheap. But it does cost money, and given how little profit most malicious actors make, this simple idea could deter many of them from targeting your company. At worst, communicating by mail means that malicious actors are slowed down by the need to print letters, buy stamps and bring the sealed letters to the post office.
- Deliver alerts through a mobile application. While there are daily reports of corporate database breaches, we hear much less about mobile applications being hacked to the point of sending their users an evil notification. If your customers have the application installed, it may be an option to send a data breach alert through a message feature on the mobile application. Most malicious actors will not have the technical skills to hack into the backend, and hiring skilled hackers will significantly increase the costs of the attack.
Both options require you to only establish costly signaling channels with your customers. This means limiting your cheap signals – such as email communications – with your customers to ensure that an email about something so important as a data breach would seem out of the ordinary.
Digital footprint monitoring to detect fake websites is another essential measure you can take. By using digital risk protection services, your company can be alerted when phishing sites are launched on the internet. This allows you to take down the website, sometimes even before it makes its first victim. Prevention will always be cheaper and faster than managing the crisis of a data breach.