Ransomware is a growing threat to any organization, government or business. In Canada alone, it is estimated that ransomware attacks and the associated downtime cost our economy CAD$2.4 billion in 2020.
HOW RANSOMWARE ATTACKS WORK
Spread as malware through emails and insecure download links, ransomware programs embed themselves in the computer systems of firms. Ransomware programs then begin the process of encrypting sensitive and secure data, and putting it behind lock and key. Only by paying a ransom to the group responsible for the attack can this data be unencrypted.
The new tactics of ransomware groups
As security has improved and firms began to hold out on paying the ransoms, ransomware groups have developed new tactics. Since December 2019, ransomware groups have started to exfiltrate a copy of the data they encrypt. They then threaten to auction off the stolen data to the highest bidder, or to leak it to the public should organizations refuse to pay their ransom. The majority of ransomware groups appear to prefer the latter, to create the most chaos for targeted uncooperative firms.
Targeting vendors and partners of hardened targets
To better understand this worrying shift, we parsed the websites of the 9 ransomware groups that have a presence on hacking forums or are discussed in news reports. While profiling the 281 firms that had their data put up for auction or leaked online so far in 2020, we found that this shift was accompanied by a new threat.
It appears that firms that typically have long supply chains, multiple business connections and many VIP clients seem to be abnormally targeted by ransomware groups. This is because one successful attack on a firm in any given supply chain can reveal sensitive information about the individuals and organizations a company does business with. This increases the value of a single ransomware attack well above and beyond the data about the targeted firm itself. This suggests that ransomware groups do not target companies at random.
A generalized problem across many industries
There does not seem to be one industry that is specifically targeted by the supply chain attack. D*** M*** LLC, a cybersecurity firm based in Maryland, for example, was targeted for the data it holds on its notable clients including NASA, and Fortune 1000 companies.
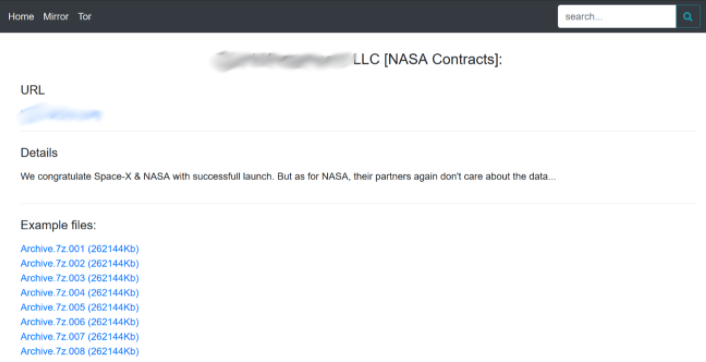
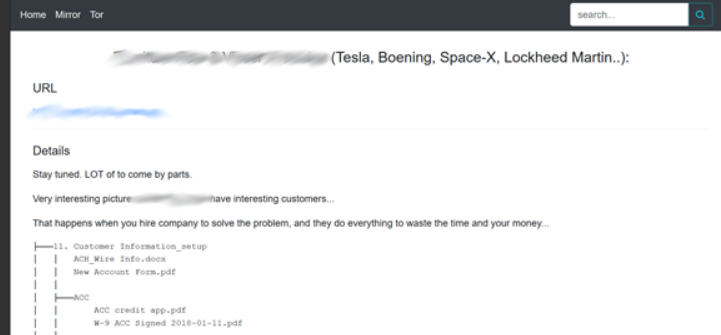
The ransomware group responsible for the attack against D*** M*** LLC, Dopple, orchestrated a similar ransomware attack against V*** P***. This firm is a small aerospace and defense manufacturing contractor based in Colorado, counting no more than 50 employees. As a contractor, the firm provides parts for many larger corporations in the automotive and defence industry, including Tesla, Boening, Space-X and Lockheed Martin.
These are firms that are at the top of their industries, and that likely boast strong internal cybersecurity infrastructure. Nonetheless, due to an insecure link in their supply chain, sensitive documents pertaining to their business interests were leaked. As the saying goes, a chain is only as strong as its weakest link.
The financial industry is also impacted by ransomware groups. G*** is an accounting firm in Toronto that was recently targeted by the ransomware group Revil. According to Revil’s blog, company files, accounting documents of clients, credentials to login into the clients’ bank accounts and audit reports were leaked when the firm refused to pay their ransom.
Although G*** is a small accounting firm counting fewer than 10 employees, they service dozens of other small businesses in Ontario, based on the files leaked by Revil. With just one insecure link in the chain, ransomware groups compromised the financial, personal and other sensitive data of all other businesses a firm works with.
VIP clients
Beyond major business partners, storing high-value customer data can also make some firms attractive targets to ransomware groups. Law firms for example are a very valuable source of data for malicious actors. G*** S*** M*** & S***, a major entertainment and media law firm based in New York, was targeted by the ransomware group Revil.
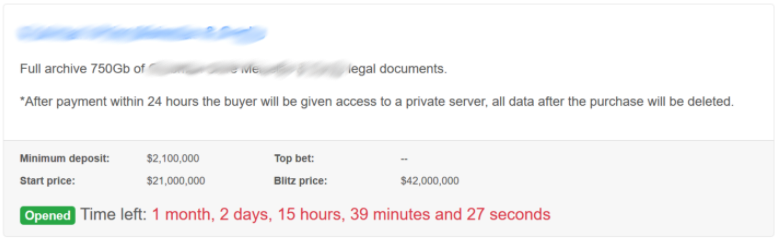
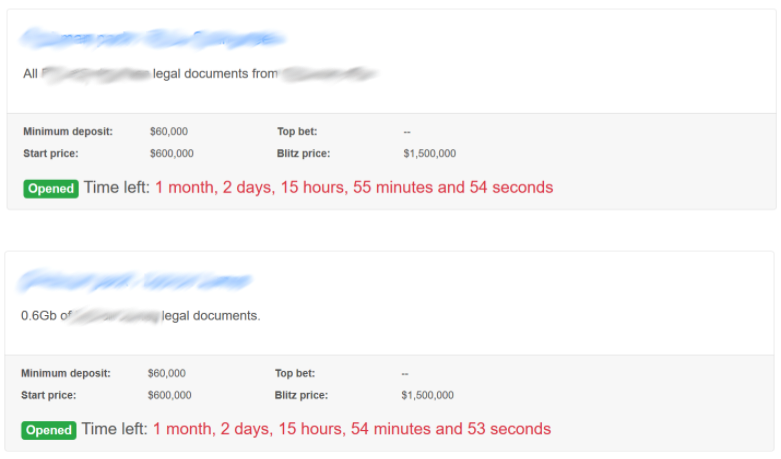
In this attack, over 750 gigabytes of data were allegedly stolen, according to Revil. Instead of threatening to leak the data to the press, Revil is holding the data at auction, allowing the sensitive information to go to the highest bidder. These include the profiles of several VIP clients
What can you do to protect your company?
The validity of any of the claims of ransomware groups are difficult to assess, unless the exfiltrated files are leaked. However, the risk of having a vendor or partner targeted by ransomware groups should be a concern for major firms.
The risks of ransomware targeting your firm can not be solely managed by your own internal security systems and procedures. In a globalized economy, with supply chains and clients the world over, a security compromise targeting your data can happen anywhere, without any fault on the part of your businesses.
Firms can mitigate their risks by extending their digital footprint monitoring. Best practices suggested that companies should monitor their own digital footprint on the dark, deep and clear web using commercial services like those of Flare Systems. Companies should now include their vendors and partners names, URLs and other identifiers in their monitoring systems of digital footprint. This will enable companies to understand if these vendors are partners are vulnerable to attacks and make sure that no confidential information is shared with those that have weak security.
Companies should also ensure that their digital risk protection providers are monitoring ransomware group websites. These websites provide early and public warnings that confidential data is about to be leaked.
With automated alerts and deep monitoring of the darkweb, including marketplaces, forums, and chatrooms through our proprietary tools, Flare Systems is well positioned to offer these security solutions to firms eager to monitor their digital footprint. For more information on the risks presented by ransomware and how to prevent it, do not hesitate to contact [email protected].
The validity of any of the claims of ransomware groups are difficult to assess, unless the exfiltrated files are leaked. However, the risk of having a vendor or partner targeted by ransomware groups should be a concern for major firms.
The risks of ransomware targeting your firm can not be solely managed by your own internal security systems and procedures. In a globalized economy, with supply chains and clients the world over, a security compromise targeting your data can happen anywhere, without any fault on the part of your businesses.
Firms can mitigate their risks by extending their digital footprint monitoring. Best practices suggested that companies should monitor their own digital footprint on the dark, deep and clear web using commercial services like those of Flare Systems. Companies should now include their vendors and partners names, URLs and other identifiers in their monitoring systems of digital footprint. This will enable companies to understand if these vendors are partners are vulnerable to attacks and make sure that no confidential information is shared with those that have weak security.
Companies should also ensure that their digital risk protection providers are monitoring ransomware group websites. These websites provide early and public warnings that confidential data is about to be leaked.
With automated alerts and deep monitoring of the darkweb, including marketplaces, forums, and chatrooms through our proprietary tools, Flare Systems is well positioned to offer these security solutions to firms eager to monitor their digital footprint. For more information on the risks presented by ransomware and how to prevent it, do not hesitate to contact [email protected].