
We updated this article on October 19, 2023, to include information about META malware.
While phishing attacks and malicious website links often lead to ransomware attacks, many deliver other types of malware. Over the last few years, attackers increasingly rely on infostealer malware variants to obtain employee credentials. According to Accenture’s research, the RedLine stealer malware was the most popular variant, accounting for 56% of infostealers in July 2022 and 48% in October 2022. In response to credential-based attacks, organizations implemented multi-factor authentication (MFA), but resourceful threat actors now barrage users with MFA notifications in MFA fatigue attacks.
More recently, the newer stealer malware META has emerged and is becoming more popular. Threat actors advertise META as an “improved” version of RedLine.
As you continue to defend your company’s IT environment, you should understand what an infostealer malware is and how the RedLine stealer malware works.
What is Stealer Malware?
Information stealer, or infostealer, is a form of Remote Access Trojan, malware that collects and forwards user information, like credentials saved in the browser, to the malicious actor. Attackers typically start with a social engineering attack method then infect the device using malicious attachments, websites, and ads.
Typical data collection methods include using:
- Browser Exploitation Framework (BeEF): control browsers or applications (particularly for saved cookies and passwords in the browser that can be used to exploit services and launch session replay attacks)
- Form grabbers: intercept and copy data that users send in forms
- Keylogging: recording the keys that people strike on their keyboards
Most infostealer malware variants target:
- Online banking services
- Social media sites
- Email accounts
- FTP accounts
- eCommerce platforms
- Cryptocurrency wallets
What is RedLine Stealer?
Originally discovered in March 2020, attackers initially delivered the RedLine malware in an email campaign, spoofing a legitimate coronavirus-cure research company email address. The RedLine Stealer infostealer variant offers a customizable file-grabber, enabling attackers to collect credentials from web browsers, cryptocurrency wallets, and applications, including:
- Chromium browsers
- Gecko-based browser, like Mozilla Firefox
- FTP clients
- Instant messaging applications
- VPN applications
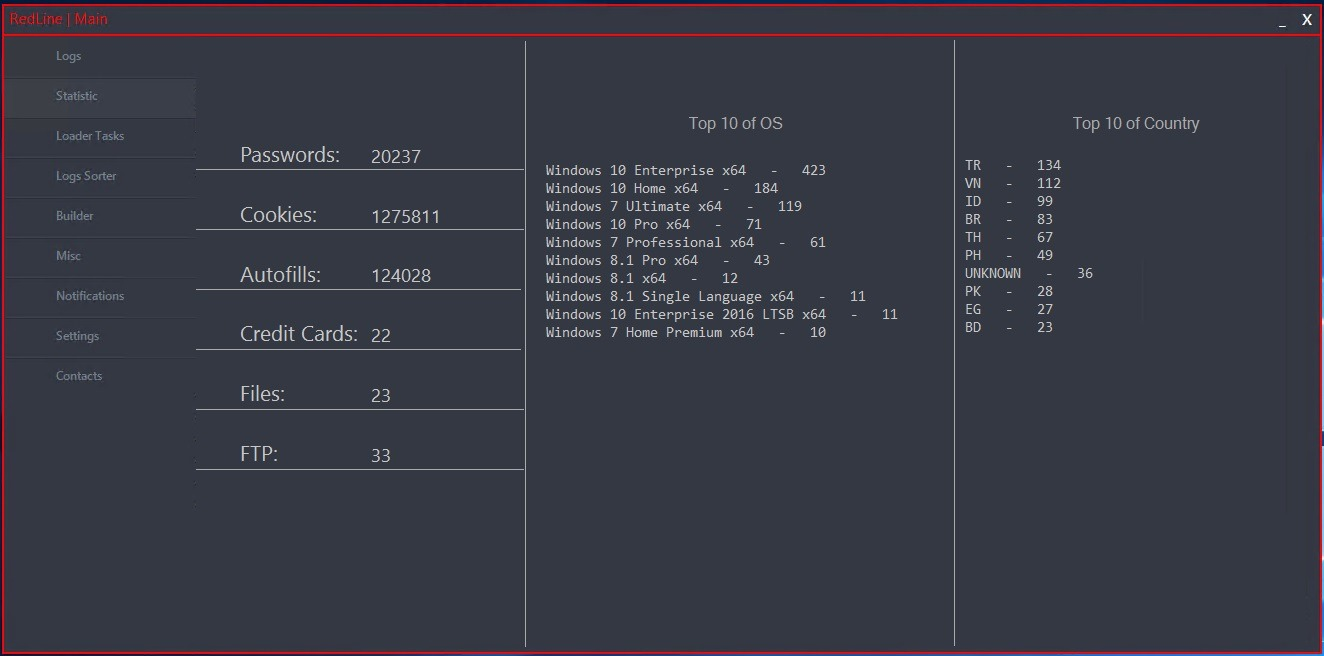
RedLine collects the following information from users’ browsers:
- Logins and passwords
- Cookies
- Auto-fill form fields
- Credit card data
- Browser history
Further, RedLine Stealer also collects information from the compromised device, including:
- IP address
- Country
- City
- Current username
- Hardware Identification (HWID)
- Keyboard layout
- Screenshots
- Screen resolution
- Operating system
- User Account Control (UAC) settings
- User-Agent
- PC hardware information
- Installed anti-virus tools
- Data about privileges running
- Data/files from common folders
Although RedLine Stealer has been around since 2020, malicious actors continue to deploy it. In January 2023, researchers observed malicious actors delivering the malware variant using OneNote files.
As organizations adopt more cloud-based technologies, malicious actors will increasingly seek to steal credentials and evolve their use of the RedLine Stealer malware.
How Threat Actors Purchase and Use RedLine Stealer
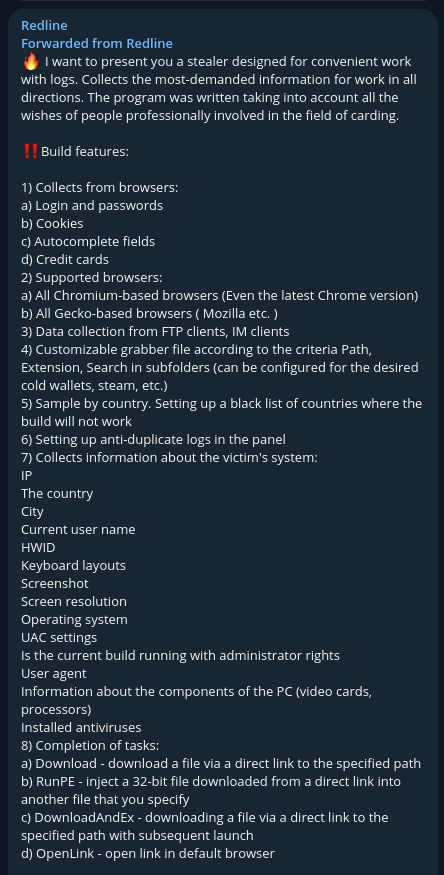
RedLine Stealer is a Malware-as-a-Service (MaaS), so threat actors can purchase it then sell the stolen data on dark web forums.
What is Malware-as-a-Service (MaaS)?
Malware-as-a-Service (MaaS) is the process of malicious actors following the Software-as-a-Service (SaaS) subscription business model to make money from their malicious code. The threat actors offer lifetime licenses or monthly subscriptions that include:
- Malware program
- Command and Control Center (C&C) infrastructure
The MaaS vendors do the same thing that SaaS vendors do:
- Offer access to an online platform
- Generate user accounts so customers can manage the attack
- Provide technical assistance when customers need help with the platform
With the subscription, malicious actors can receive, sort, and extract information from compromised devices’ logs.
How Does the MaaS Ecosystem Work?
The MaaS ecosystem consists of online forums acting as marketplaces. Three basic malicious actors need to interact:
- Someone selling a malware
- Someone selling the stolen data
- Someone who wants to use the stolen data to engage other crimes, like fraud
Malicious actors advertise their malware on forums with listings that define the malware’s functionality, including:
- Data it collects
- Supported software
- Data collection locations
- Customization capabilities
- Platform’s settings
- Tasks it performs
After purchasing and deploying the malware, the customers then sell that data in dark web forums, like the Russian Market, with listings that typically include:
- Stealer malware family
- Device operating system
- Device country of origin
- Victim internet service provider
- List of service credentials available
- Archived directory content
- Device infection date
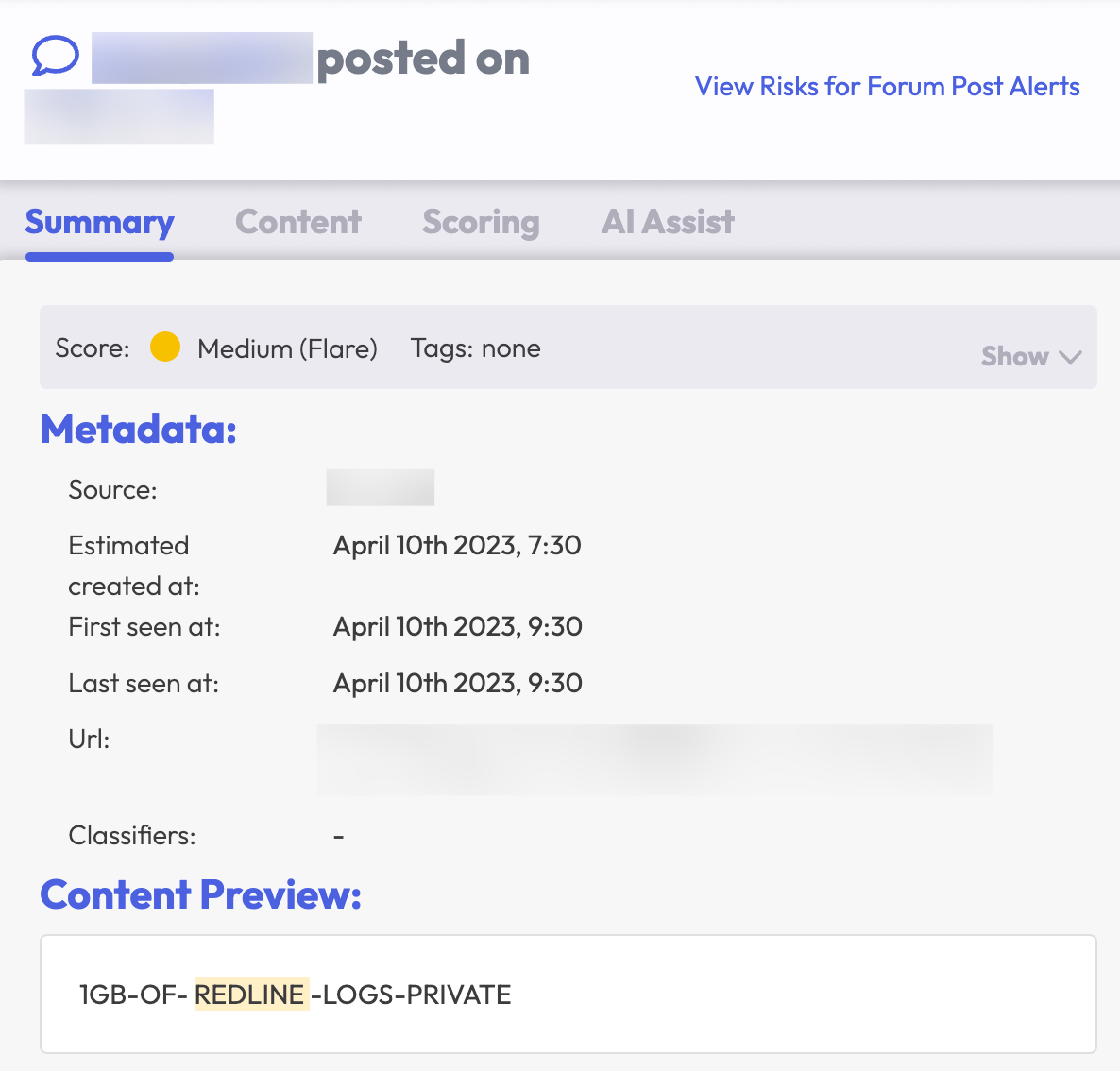
Cybercriminals, like those who specialize in online fraud, purchase these records so that they don’t have to steal the information and can focus on their illicit business model.
Want to learn more about the lifecycle of a stealer malware attack? Take a look at our report, Dissecting the Dark Web Stealer Malware Lifecycle with the MITRE ATT&CK Framework.
RedLine Stealer and Telegram Channels
Malicious actors increasingly use the Telegram messaging app to purchase and deploy their RedLine Stealer malware. Various factors contribute to why this instant messaging platform is so popular with threat actors:
Illicit Telegram Groups Can Provide Greater Anonymity
Dark web sources can be intensely monitored by cybersecurity teams and various law enforcement agencies. Though Telegram channels could also be monitored, there are some elements that establish a sense of safety:
- Channel can have “disappearing messages” that can delete messages after a certain amount of time like between 24 and 72 hours
- There is a rapid flow of messages, so even if existing messages still exist, they can be pushed away by the new messages, so the interactions feel “less permanent”
- Telegram’s strict privacy policies can allow threat actors to feel more secure (whether that is true or not)
Illicit Telegram Groups Can Be Easier to Use
Compared to the difficulties of connecting to dark web sources, Telegram is much more reliable:
- The service only requires a mobile phone number (which can be hidden)
- Telegram channels do not require a domain to offer services and tools for sale and can be used by downloading the app
- As long as the Telegram service remains online, threat actors can continue to stay online
In addition, Telegram’s growth as a go-to messaging platform makes it a target for attackers. With more users on Telegram, attackers can cast a wider net. Additionally, since anti-virus tools often fail to scan the application, it offers fertile data soil. For example, malicious actors disguised one RedLine variant as a Telegram installer to evade detection.
RedLine Stealer: How to Protect Your Organization from It
Protecting yourself from the RedLine Stealer requires you to proactively mitigate risks.
Provide Cyber Awareness Training
Most RedLine Stealer infections begin with a social engineering attack. As part of your security awareness training program, you should ensure that employees learn to:
- Detect and report phishing attacks, including a reminder not to click on any suspicious links or documents
- Store passwords securely, such as in an encrypted password manager rather than their browser
- Implement and use MFA
- Download apps only from trusted sources, like the App Store or Google Play
- Install anti-virus software on all devices
Install Security Updates
Malicious actors can use vulnerabilities in operating systems and trusted applications. You should implement a vulnerability and patch management process to push security updates to all devices connected to your networks and systems.
Proactively Threat Hunt
Security researchers provide the Indicators of Compromise (IoCs) in their reports. You should use this information to proactively look for potential infections across your IT environment.
Monitor the Dark Web and Illicit Telegram Channels
By scanning dark web forums and illicit Telegram channels, you can proactively identify:
- Credentials for sale
- Infected devices
- Mentions of your company indicated targeted threats
How Flare Can Help Detect Redline Stealer
With Flare, you can automate the dark web and Telegram monitoring for context that enables threat prioritizations. Our Artificial Intelligence (AI) analyzes malicious actor behaviors to proactive identify threats, and our actionable alerts help you filter through the noise so you can focus on what matters most.
With Flare’s automation, you can monitor the dark web and Telegram channels at speed and scale for comprehensive visibility into the risk that your digital footprint creates. Our solution provides Telegram monitoring across hundreds of Telegram channels,giving you the ability to track search terms for stolen credentials and data leaks.
To get started monitoring your digital footprint and protecting your business, sign up for your free trial today.



