
To hide their true identity, malicious actors route traffic through relays called proxies. Since the criminal underground abounds in offers for proxy services, Flare Systems’ threat intelligence team investigated the Canadian criminal underground to identify which proxies may impact your company’s security, as well as the business model approach embraced by malicious actors.
Understanding the different types of proxies
1. The data center proxy
The most popular type of proxy advertised on the criminal underground is the data center proxy. Malicious actors use stolen credit cards – or simply pay with cryptocurrencies – to rent out virtual servers. Their bandwidth is then resold based on the volume of traffic or the number of concurrent connections. Some malicious actors also hack into virtual servers and discreetly install proxy servers on them to abuse their resources, without their owner’s knowledge or consent.

2. Residential proxies
Residential proxies are hosted on IP addresses that belong to large telecom companies and appear to be home connections to anyone who monitors their traffic. Malicious actors set up residential proxies by hacking IoT and home computers, and installing secret proxy software on them. Criminals can also purchase these IPs and bandwidth from telecom companies who are turning a blind eye to the real use of the service, as described by KrebsOnSecurity.
3. LTE / Mobile / 4G / 5G proxies
LTE / Mobile / 4G / 5G proxies are promoted as cutting edge. These refer to mobile phones and use IP addresses labelled as mobile data. Similar to residential proxies, malicious actors use them to simulate that their connection is coming from a personal mobile phone. Mobile proxy providers purchase bulk data from telecom companies under false pretenses, or install malware on Android phones and hijack the phone owners’ connections. As mobile data plans are limited (especially in Canada), the price of mobile proxies is the highest of all.

Rotating, shared or private. What should you know?
Many malicious actors can hide behind the same proxy to launch their attacks. This is, however, likely to make their attack easier to detect. This is why rather than use shared proxies, malicious actors may pay more to rent private proxies. Private proxies enable full control, as they are exclusively used by one user at a specific time. They deliver more security and prevent bandwidth overload compared with shared proxies. They also prevent one malicious actor from polluting an IP address while it is being used by others.
A rotating proxy is a service that updates the malicious actor’s IP address each time an online request is made. As a result, a malicious actor can collect a million different web pages from a million different IP addresses. By the time an IP address is flagged as abusive, the criminal has already moved on and cannot be blocked through IP filtering. Because rotating proxies require a large number of IPs, they are more often offered for data center proxies which are cheaper.
How malicious actors use private rotating proxies to hide their tracks
Malicious actors take advantage of proxy anonymity to seamlessly connect to servers, and to prevent being identified as a high-risk source of attack (ex: Russian malicious actor). Considering the high number of benefits various proxy combinations provide, malicious actors can mix and match, depending on their specific needs as shown in the table below.
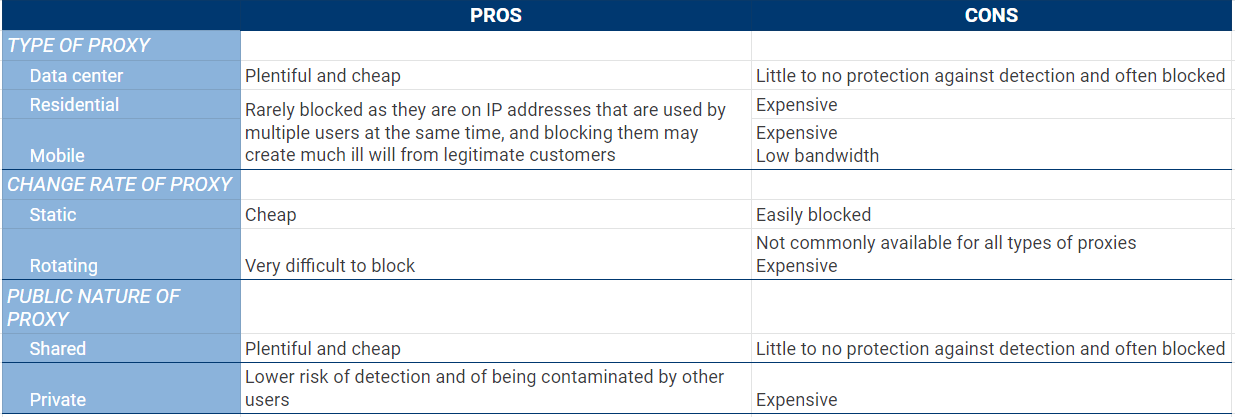
Proxies can be manually configured to influence how victims perceive their traffic. Malicious actors that use residential and mobile proxies, especially when coupled with private and rotating proxies, become moving targets, often hard to shut down. Even though they are expensive, these proxies deliver the perfect cover to launch large-scale attacks, such as credential stuffing attacks.
Additionally, mobile proxies provide a significant benefit. All mobile phone internet traffic from telecom companies can only be traced back to a limited number of IP addresses with static geolocation. While one may be located in Montreal, location services will believe the mobile phone is actually located in Ontario.
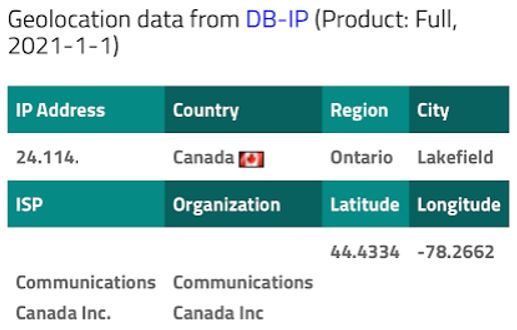
Consequently, security practices that verify a user’s location based on their IP address cannot be trusted when a mobile IP address is used.
Lessons learned
Proxies are not only used by malicious actors for illegal activities. They are legal services, often recommended to maintain online activity secure, because they can be easily installed on most devices and browsers. A number of companies use proxy servers as intermediaries to control internet traffic and reduce breaches, or for social media management and data collection, while private users might use them to access streaming services or websites that restrict access to their geographical location.
Canada does not appear to be a major source of proxies. We found only a limited number of Canadian providers, and even then, there is no guarantee that they can in fact offer Canadian residential and mobile proxies. Should law enforcement decide to target that small group of actors, it could become very difficult for malicious actors to purchase Canadian proxies. Conversations with law enforcement agencies could be started to discuss their interest in targeting this type of malicious actors.
Even though proxies are now easily available, it is important for your company to continue to implement security solutions that monitor and filter connections based on IP addresses. These solutions will not necessarily protect your company against sophisticated attacks, but will raise the bar for malicious attackers. This ensures that your company is not a low hanging fruit, and does not become a soft target for malicious actors. Therefore, in today’s world, the role of these solutions is more about lowering the number of attacks, rather than decreasing their odds of success.
Above all, collecting reliable intelligence on malicious actors through active monitoring of the criminal underground is an essential part of a good cybersecurity hygiene. This ensures that you remain informed about the tactics and methods of malicious actors, and can better understand what your security tools can and cannot do to protect your digital assets.
Luana Pascu contributed to this research report.



