Five years ago, Avast published a blog post that analyzed a database of 2,000 passwords used by hackers. It found that hackers use very easy to crack passwords just like most people. In fact, their most common password was hack!
In this blog post, we follow-up on our previous post on 46M cracked passwords. This time however, we analyze the passwords used by 57,000 fraudsters online. We find that fraudsters are getting better at choosing passwords. We also explain how cracking fraudsters’ passwords provide clues about fraudsters’ identities and their methods.
Password analysis of regular people
Over the last 10 years, 14 studies have analyzed leaks of password databases. The table below shows the evolution of the TOP 10 most common passwords found in those leaks.
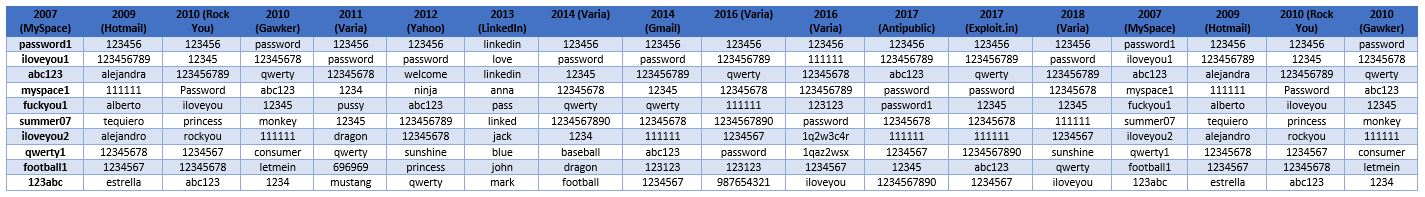
The table shows that the most common passwords change over time. They appear on average in 3 of the TOP 10 lists. Most of them are composed of numbers (ex. 123456), simple words (ex. password) or words related to the source (ex. myspace1 for the MySpace leak).
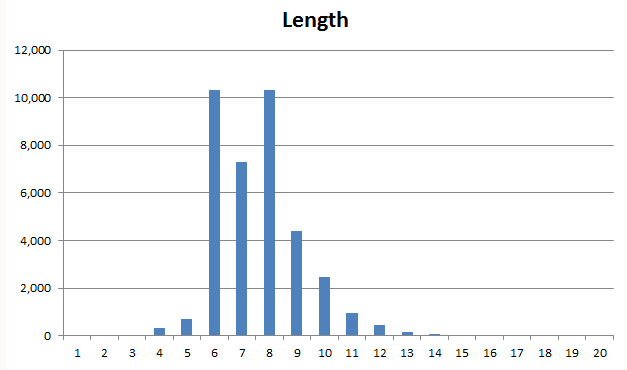
Passwords tend to be fairly short. Most passwords are between 6 and 10 characters long as shown above in Troy Hunt’s analysis. Other analyses show passwords as long as 225 characters but these represent less than 0.01% of all passwords.
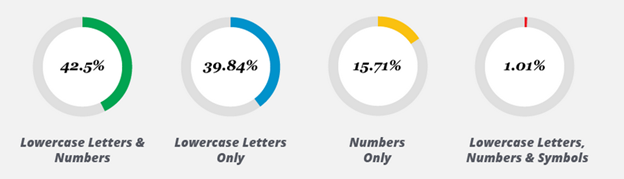
In addition to being short, most passwords are either composed of numbers only, lowercase letters only or a mix of both. About 1% of passwords follow the best practice of also mixing in symbols. Combined, password length and composition explain why security researchers (or hackers) can usually decrypt over 80% of leaked encrypted passwords.
What about fraudsters?
In May of 2019, the OGusers forum database was leaked online (it was leaked again this week). The forum discusses how best to scam large corporations and has over 110,000 members. One classic scam discussed was how to manipulate a company to issue a refund even when no product was returned.
Using Google Cloud instances and Hashcat, we managed to crack 57,046 passwords. Our techniques include multiple public and private dictionaries and statistical analyses of cracked passwords. Wired explained in an interview some of the techniques that we used.
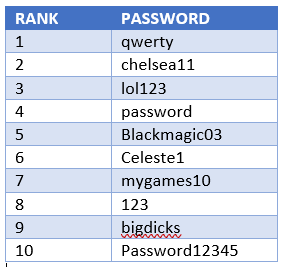
Hackers admittedly used some very weak passwords such as qwerty and 123. 7 out of 10 of their TOP 10 most common passwords were however not found in other TOP 10 lists. This suggests that fraudsters may choose their passwords differently than regular people. Their most common passwords are slightly more complex as they contain capital letters.
These 10 common passwords combined represent 3% of the passwords we cracked. While the most common passwords are weak, they represent only a small share of all the passwords used. People still use password as their password; fewer and fewer people are choosing it however.
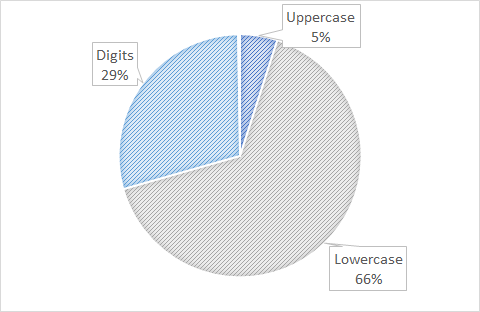
Fraudsters’ passwords contain a majority (66% of password characters on average) of lowercase letters. They also contain many digits but very few uppercase characters. Passwords contain on average no special characters.
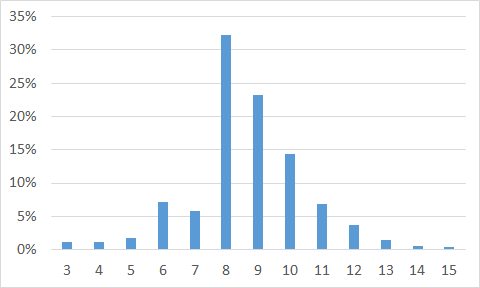
Fraudsters’ passwords appear to be mainly between 6 to 10 characters long. The longest cracked password was 26 characters long (abcdefghijklmnopqrstuvwxyz, qwertyuiopasdfghjklzxcvbnm, gggggggggggggggggggggggggg and stoplookingatmypassword123). These passwords followed easy to guess keyboard patterns or groups of dictionary words followed by numbers.
Why crack fraudsters’ passwords
While cracking passwords is fun, it can more importantly help us better understand malicious actors for two reasons.
Clues about fraudsters’ identity
Many fraudsters use personal information (ex.: location, pet’s name, employer) as their password. By cracking passwords, we find these bits of information that steer investigators, or at least help build hypotheses.
We suspected that a number of OGusers members were Canadians. We found that some used passwords like Canada or Montreal. Now, it is possible that a UK fraudsters would randomly choose Montreal as their password. But what are the odds compared to those of a Montreal native choosing Montreal as their password?
Enhancing our understanding of fraudsters’ methods
Many actors create multiple identities online. They do so to scam other fraudsters, fake references and praises or even recover from being banned. Connecting identities is an important step of intelligence operations. It reduces the number of actors to monitor and enhances our knowledge of what they say and do.
We applied the Dropbox ZXCVBN algorithm (see our previous blog post) to identify complex passwords reused across accounts. These passwords are so complex that two people would never have randomly chosen to use them; the owner of the account must be the same.
Passwords with a level of 4 (highest score, unlikely to be chosen randomly by two people; for example ZXCasdQWE123) are associated with 1.3 accounts on average; passwords are associated in one case with 128 different accounts. About 10% of level 4 passwords are associated with more than one account. This provides evidence that many malicious actors control more than one accounts on online platforms. This figure is an underestimate of course. Malicious actors could control more than one account with very simple passwords. The word password for example is used by 133 accounts. The 10% baseline is useful still to model forum internal fraud and deception.
Future research
What kind of fraud and deception takes place will be the focus of future blogs. We expect however to find that malicious actors steal from and abuse each other by making false promises and using different accounts to prop up their promises.
Our Firework solution provides you with a list of all the fraudsters’ passwords we have collected. You could today match these passwords against your employees and customers. When a level 4 password match is found, it could very well indicate that a malicious actor is reusing their password on your platform. That actor should be watched very closely as they are likely to abuse our clients or their customers.
Contact us at [email protected] to find out more or to book your free 2 months digital risk protection trial to help you deal with the current COVID-19 crisis and take back your peace of mind.