A well-known malicious actor recently published on a forum the information of millions of customers of a popular T-shirt printing service. While no passwords were leaked, the criminal did publish the email addresses and personal information (names, addresses, and phone numbers) of millions of people.
Why is this leak significant? First, this basic information is worth more than one may think. Journalist Mat Honan recounts how in 2012 his whole digital life was erased by malicious actors who took over his iCloud account, and erased his devices. All they needed were his home address and the last four digits of his credit card. How the malicious actors obtained the second information is worth a read.
It turns out, a billing address and the last four digits of a credit card number are the only two pieces of information anyone needs to get into your iCloud account. Once supplied, Apple will issue a temporary password, and that password grants access to iCloud.
So publicly published names and addresses, can, in some cases, have a dire impact on victims. Whether leaks contain both usernames and passwords, or simply usernames and other information, all leaks should be analyzed for risks to your company, employees and customers. Proactive mitigation measures should immediately be put in place.
Going back to our news story, the other noteworthy element is the timeline between the attack and the public release of information. According to the article, the data was stolen in June 2020. The company issued a public disclosure in July 2020, a short time after the incident. The stolen data apparently started circulating in December 2020 on private forums and Telegram channels, before ending up on a public forum in January 2021.
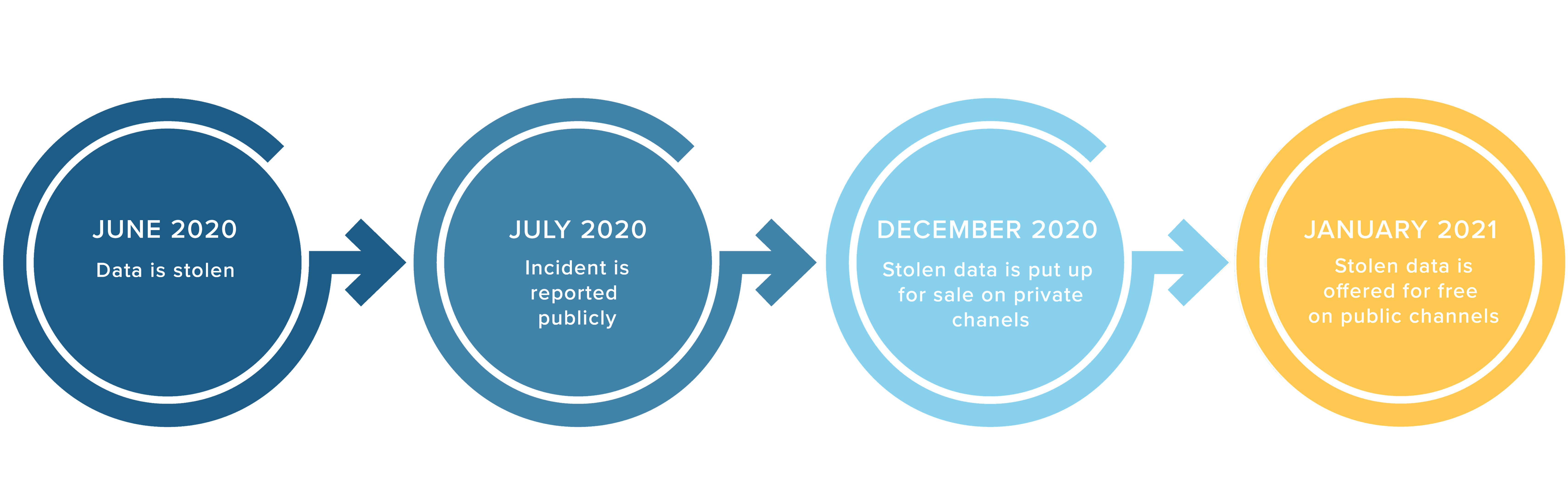
If this narrative is true, then the malicious actors who purchased the information in December 2020 only had a few days (including the holidays) to launch attacks before anyone could. The value of the data that was sold in December is therefore quite limited, and may contribute to lowering the price of future data leaks for sale. If their vendor cannot guarantee that the information will remain private, why should anyone pay for it?
If the data was indeed sold in December 2020, this raises a question about what happened to it between June 2020 and December 2020. The truth may lie in the fact that massive leaks are now occurring at an increasing rate. Malicious actors who steal this information may be overwhelmed by the quantity of data they have to put up for sale, or may want to wait until a window opens up when there is less competition. Two actors putting up large stolen databases for sale are likely to be competing for the same buyers, and earn a lower price for their data.
Another hypothesis is that proactive incident reporting meant the company, and its users, would be more alert to potential fraud around the time of the data leakage. The company’s proactive reaction may have forced the malicious actors to postpone their plans to target its customers.
The unfortunate consequence is that companies who monitor the clear and dark web for signs of their stolen data may need to do so for months, if not for years after the incident. In this case, it would have been a mistake for the company to stop the monitoring process after just three months, on the wrongful belief that it was in the clear and the stolen data would never be released. This oversight could have cost the company its reputation, damaged its brand, and greatly affected its customers.
Conclusion
The silver lining in this news story is that criminal underground infighting has made it clear that the stolen data was indeed being sold and distributed online, and that monetizing this data would be difficult. There is indeed a high level of competition between malicious actors in selling the stolen personal and financial information. In this case, this war made it possible for all to learn that the company’s data was up for sale online. Unfortunately, this also means that a larger pool of criminals may be looking for this data, and that the number of attacks may be increasing.
Still, knowing about a threat, whether from a small or large group of malicious actors, is a first and necessary step to mitigate its risks. The company’s customers should protect their credit records, and use two-factor authentication (2FA) whenever possible, to prevent unauthorized access into their accounts. Whenever possible, users should avoid sharing their real information to protect themselves against future attacks.
Following an incident, companies should set up continuous monitoring to detect as soon as possible if the lost data has been posted online. Hiring a Digital Risk Protection (DRP) provider with access to private forums will enhance your security, and provide you with a few weeks of advanced knowledge whether your data is circulating online or not. Unfortunately, it seems that the truth always wants to come out. Once leaked data starts showing up for sale on private forums, it is likely to end up in the hands of the public in a matter of weeks, if not days.