
What Is An Attack Surface?
An attack surface is the total number of all possible attack vectors (or points) where an attacker or unauthorized user can access a system and enter or extract data.
Attack surfaces can be split into two different categories.
1. Physical Attack Surface
A physical attack surface area for an organization includes all endpoint devices such as desktops, hard drives, laptops, mobile devices and usb ports.
2. Digital Attack Surface
A digital attack surface area for an organization includes all hardware and software that connect to the organization’s network. Some examples of these surfaces include, applications, code, ports, servers, shadow IT and websites. Due to the wide variety of digital attack surfaces, there are multiple situational entry points that can lead to vulnerabilities such as poor coding, weak passwords, poorly maintained software and default operating system settings. An organization can also break up a digital attack surface into a classic digital attack surface and an external attack surface.
Here’s a visualization of how an external attack surface differs from our conventional understanding of an digital attack surface:
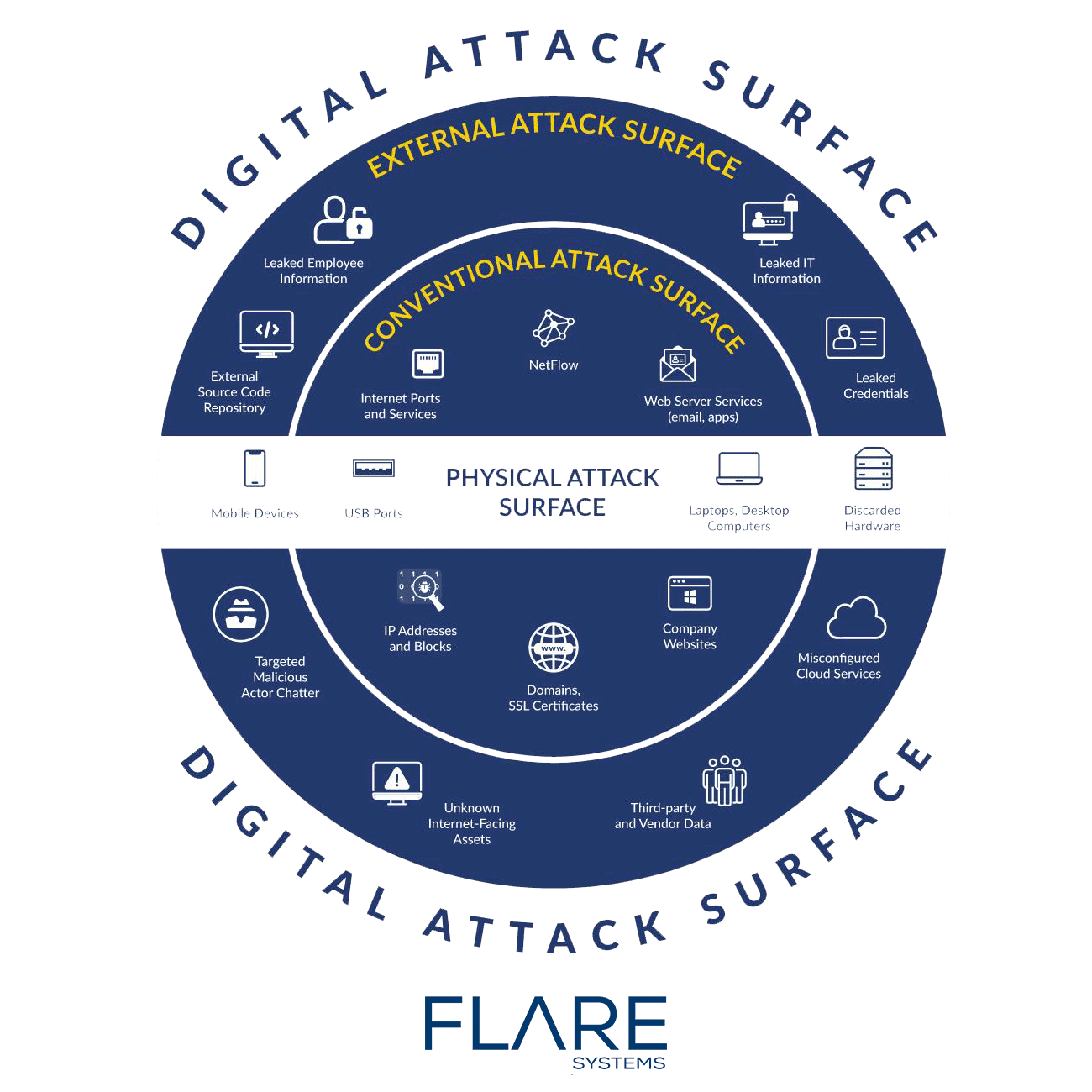
The attack surface includes all vulnerabilities and encompasses the entire “surface area” of an organization that is susceptible to malicious actors.
Flare’s Digital Risk Protection software specifically focuses on External Attack Surface management and provides monitoring of anonymous sharing sites and Github for source code, detection of technical data leakage and identification of misconfigured servers.
What is an Attack Vector?
An attack vector is a method or pathway used by a hacker to access a system. Here are a few examples of attack vectors:
- Misconfiguration
- Malware
- Ransomware
- Phishing
- DDOS Attacks
- Compromised Credentials
- Malicious Insiders
- Missing or Poor Encryption
- Exploiting unpatched vulnerabilities
The relationship between attack surface and attack vector being: the more attack vectors your company is vulnerable to the larger your attack surface will be.
How does an Attack Surface Differ by Organization Size?
The size of the organization generally dictates the size of an attack surface. Small, mid-sized and large corporations can all be victims of cyber attacks. The issue with small and medium sized businesses, however, is exacerbated due to an ever increasing cybersecurity skills gap, an increase in cybersecurity attacks in general and an unawareness of the company’s overall digital footprint.
How can you define your organization’s attack surface area?
Organizations must start defining their attack surface by visualization. Visualization includes identifying weaknesses, assessing vulnerabilities and determining user roles and privilege levels and communicating them through pictures and notes. As the company starts reviewing and mapping for visualization it will start to identify different entry points such as:
- User interface (UI) forms and fields
- HTTP headers and cookies
- APIs
- Exposed unpatched endpoints
- Files
- Databases
- Other local storage
- Email or other kinds of messages
After the overall mapping is complete, organizations can start to categorize these points by their preferred methods.
As there can be numerous entry points, this data can also be split into categories by function, design, and technology. Examples of categories include: login/authentication entry points, transactional interfaces/APIs and business workflows etc.
As discussed before, companies can categorize by physical attack surface, which would include on premises systems and devices etc and digital which would include the cloud. Organizations that are mostly digital can also organize their visualization by breaking up the digital attack surface into a general bucket and an external attack surface bucket.
After categorizing the mapping, organizations can begin to assess risk levels by observing which users have access to which data and how. The assessment process can make some obvious, such as, employees and data related to the cloud can be more at risk due to remote access. In any case, when this assessment is complete organizations will know the particular behaviours of users/ departments and will know attack vectors by the levels of risk and category functions.
What is Attack Surface Management ?
Attack surface management (ASM) is the continuous discovery, monitoring, contextualization and prioritization of the sum of all the public information related to your organization that can be leveraged by a malicious actor. An attack surface can be managed through cybersecurity practitioners, tools and platforms to mitigate all current and future cyberthreats.
How to Reduce the Size of Your Attack Surface
It is not enough to only manage the attack surface that you have currently, it is also essential for organizations to actively try to reduce the size of their attack surface. Below are six tips to do just that:
1. Zero Trust Model
One of the fundamental issues that can occur in organizations is access control. In this model an organization ensures that only the right people have the right access to the right resources. This prevents unauthorized access to sensitive data both internally and externally. As discussed earlier in the piece, decreasing the attack surface and number of entry points is key in ensuring the security of your company. As such when an organization enforces a zero trust model, entry points (or attack vectors) are automatically decreased and the organization’s overall security apparatus is strengthened.
2. Secure-By-Design Principles
According to the Open Web Application Security Project (OWASP), one of the key aspects an organization can focus on for attack surface reduction is executing preemptive cybersecurity design decisions. In this case, the concept is similar to limiting user access to specific functions, however, this decision is taken preemptively in the design phase rather than later when risks are well defined.
3. Complexity Elimination
Unnecessary or unused software and devices must be removed or disabled from the organization. Unnecessary software or hardware can be used as entry points as these can be more prone to bad actors exploitation.
4. Continuous & Accelerated Reconnaissance
Organizations should conduct regular scanning of digital assets and data centers to spot vulnerabilities. In these scans an organization can assess cloud and on premises networks. The organization can perform this scanning manually or can also use a platform or tool to perform continuous and faster reconnaissance.
5. Network Segmentation
Tools like firewalls and strategies like microsegmentation can allow organizations to minimize their attack surface by adding barriers for malicious actors.
6. Employee Training & Education
One of the biggest potential threats to an organization can be a lack of cyber security hygiene due to inadequate training. Malicious actors in many cases are targeting people to hack into organizations and due to this cybersecurity hygiene and awareness training are important to prevent vulnerabilities.
An attack surface is an idea that all companies must be familiar with and should actively be trying to mitigate. Whether it be a digital, physical, or external attack surface understanding an organization’s current attack surface plays a key part in attack surface reduction. As there are numerous attack vectors, there are just as many ways to address vulnerabilities in an organization. As cybersecurity attacks increase in general going forward, it is imperative for organizations to use all tools, platforms, and personnel to map, assess and mitigate all digital risk associated with their attack surface.



