
Any intrusion into a network calls for a thorough analysis to give security teams cyber intelligence about different threats and to help thwart similar future attacks. However, effective incident analysis has long been held back by uncertainty and high false positive rates in intrusion detection systems that lead to slow threat mitigation.
The diamond model of intrusion analysis brings efficient, effective, and accurate analysis of incidents that companies and security teams have long lacked. Here’s a quick guide to give you the lowdown on the model.
A Diamond Event: The Model’s Atomic Element
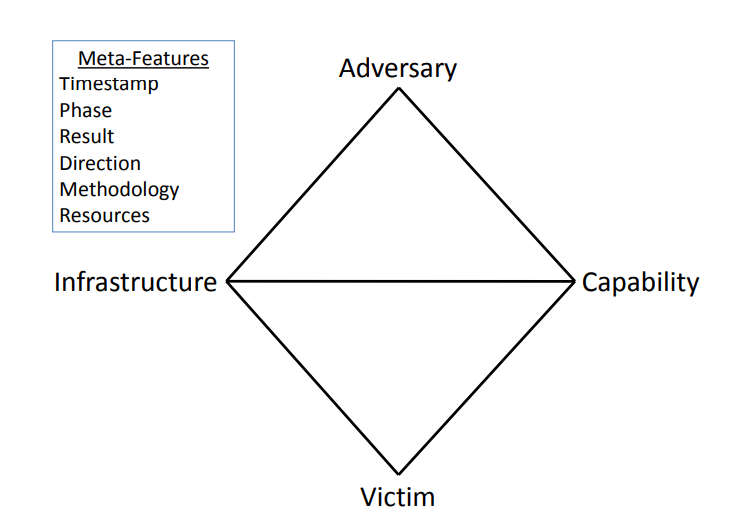
The diamond model organizes the key aspects of malicious activity into the shape of a diamond, which is visually memorable, easy to understand, and symbolizes the relationship between these key aspects. Underneath the clear image of a diamond is a more complex mathematical relationship that explains the model via game theory and other fields of math.
The diamond model defines an event as the central element necessary for four key aspects of malicious activity to occur. Any event in the model is a time-bound activity restricted to a specific phase where 1) an adversary uses 2) a capability over 3) infrastructure against 4) a victim with a given result.
An important point about how an event relates to these four main features is that most of the details about the core features remain unknown until new facts get revealed via input from additional data collected about the event. Reflecting the fact that knowledge about features depends on further analysis and good-quality data sources, the diamond model requires analysts to ascribe a confidence value that estimates the subjective confidence in the accuracy of the assessment of a given event feature.
Diamond Model: Delving Further into 4 Key Aspects of Malicious Activity
You’ve already seen what the four core aspects of any malicious event are, but let’s delve into their definitions along with examples for further clarity.
Adversary
An adversary is anyone who seeks to compromise your systems or networks to further their progress toward objectives. The definition is purposefully broad to reflect the fact that an adversary could be a malicious insider, an outside threat actor, a threat group, or even an organization. At the time of initially discovering any intrusion event, it’s unlikely you know who the adversary is.
Capability
A capability is a tool/technique deployed by an adversary in an event. The potential capabilities used by various adversaries are almost endless, but some examples include brute force password guessing, installing backdoors to establish command and control, etc.
Infrastructure
Infrastructure is not the infrastructure of your IT environment. Rather, the term relates to the communication structures that hackers use to deliver their capabilities. Examples include domain names, USB devices, compromised accounts, malware staging servers, etc.
Victim
The victim is the target of an adversary against whom they intend to use their capabilities. The model states that a victim doesn’t always need to be a person or company; it could be an email address or a domain. Given this range of possibilities, you can go more granular when defining victims by breaking them down into victim persona (people, companies) and victim assets (the attack surface that encompasses all the IT assets against which an adversary can use capabilities).
Understanding Meta-Features and Activity Threads
Each event also has so-called meta-features that are useful for higher-order intrusion analysis and grouping. These meta features include:
- Timestamp: the date or time that an event occurred (if measurable)
- Phase: One of the model’s axioms states that any malicious activity requires two or more phases carried out in succession to achieve the adversary’s intended result. Analysts can use attack trees and other frameworks to decide how many phases constitute a particular adversary operation.
- Methodology: The methodology of an event is the general class of activity observed, such as spear phishing or port scan. This differs from a capability in that a methodology is a more general class of activity rather than a description of a tool or technique.
- Resources: Another axiom in the diamond model of intrusion analysis is that any intrusion event requires one or more external resources to succeed. Examples include software, knowledge, hardware, and funds.
- Social-political: Since there always exists some sort of relationship between an adversary and a victim, this meta-feature describes that relationship in the form of an adversary’s socio-political motivations. Examples of these motivations include generating income, espionage, fraud, gaining acceptance by other hackers, etc)
This list of meta-features is non-exhaustible; your company can adapt the model to incorporate additional event meta-features based on your needs, resources, and industry-specific cyber threats.
Establishing meta features also allows for higher-level constructs in which analysts combine different events into a phase-ordered graph known as an activity thread. An activity thread assists in intuitively identifying causal relationships between different events. Where you have missing events from a thread, this helps to identify knowledge gaps in threat intelligence that you can seek to rectify.
How Useful is the Diamond Model for Threat intelligence?
The diamond model of intrusion analysis is a valuable tool for any security analysts focused on threat intelligence. This model allows those tasked with generating cyber threat intelligence to quickly analyze large amounts of incoming data and establish clear linkages between various pieces of threat information. The outcome for your security teams is a better understanding of adversary intents and strategies, which enables your business to develop proactive countermeasures against new and emerging cyber threats.
The diamond model also helps to identify intelligence gaps and lays the groundwork for the development of cyber taxonomies, ontologies, threat intelligence exchange protocols, and knowledge management. While it is a highly effective tool for threat intelligence analysts seeking to stay ahead of evolving cyber threats, bear in mind that like any model or tool, it comes with its limitations.
Complement Your Analysis with External Intelligence
If your company decides to adopt the diamond model of intrusion analysis, it’s worth complementing this analysis with other external sources of cyber threat intelligence. Using this model can identify intelligence gaps that you can often fill by better monitoring your digital footprint. This digital footprint includes external exposures that you don’t know about which pose security risks and increase the likelihood of intrusions leading to successful breaches.
Flare’s SaaS solution provides digital footprint monitoring across the dark and clear web so you can easily gather valuable intelligence about data dumps, credentials leaks, source code leaks, and more.
Get a demo and see how Flare works in minutes to supercharge your threat intel.



