Banks are all in the business of protecting savings, loans and helping invest. As a result, banks commonly share many practices and tools. In this blog post, we demonstrate how malicious actors tend to target the same group of financial institutions. This could be the result of malicious actors reusing the same techniques on multiple targets and finding that certain financial institutions are more vulnerable to specific types of attacks. This behavior of malicious actors can be exploited to cluster banks in groups to predict compromises.
Two types of malicious actors advertise stolen financial information on the darknet:
1) those that sell information from a single bank;
2) those that sell information from multiple banks.
In our experience, most malicious actors offer stolen financial information from multiple banks. The extent of that behaviour is still, however, not clear. Nor is the extent to which this can be leveraged to create actionable intelligence.
Out of the years of data collection we have, we singled out for three months (October to December 2018) the darknet advertisements for 6 of the largest Canadian Financial Institutions. We built a matrix where each dot is a malicious actor or a Canadian Financial Institution. Each tie between dots indicates that an advertisement connects the Canadian Financial Institution to one of the 30 malicious actors we identified.

A visual inspection of the graph suggests that some malicious attacks specialize in targeting a single Canadian Financial Institution. Many, however, target more than one Canadian Financial Institution. Taking a closer look, malicious actors target on average 2 Canadian Financial Institutions (Min = 1 and Max = 6). 66% of the malicious actors target more than one.
Multiple malicious actors target each Canadian Financial Institution. On average, 39% of the malicious actors in our sample target all the Canadian Financial Institution (Min = 3 and Max = 18).
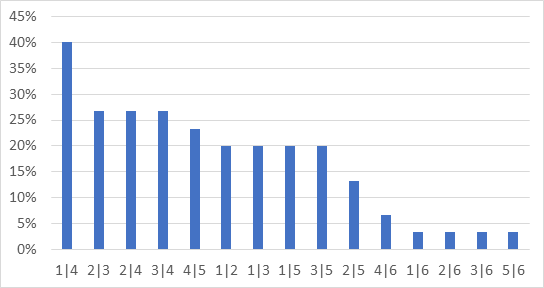
Going further, we analyzed how often malicious actors targeted the same pairs of Canadian Financial Institutions. The graph above shows that when a malicious actor targets the Canadian Financial Institution #1 (name redacted), the Canadian Financial Institution #4 is also targeted 40% of the time. At the opposite end, when a malicious actor targets the Canadian Financial Institution #5, there is only a 3% chance that it will also target the Canadian Financial Institution #6.
Conclusion
To explain our results, we offer two hypotheses. First, a majority of malicious actors on the darknet have the skills and time, or the ability to purchase exploits, to compromise multiple Canadian Financial Institutions. Second, our most logical hypothesis, malicious actors have developed tools and strategies that are based on the vulnerabilities of a specific market. Reusing passwords and phishing through spam campaign are likely to work against all computer systems including those of Canadian Financial Institutions. As a result, we may have similar vulnerabilities in multiple infrastructures.
Malicious actors leverage their exploits against one Canadian Financial Institution to expand their victim base. Looking at which Canadian Financial Institution are victimized by a malicious actor could help us guess how other Canadian Financial Institutions will be victimized in the future.
The main takeaway is that Canadian financial institutions should use proper threat intelligence to identify who their closest peers are. These peers may have adopted similar policies and defense strategies that make them vulnerable to the same types of attacks. Canadian Financial Institutions can use this information as a warning system. If a malicious actor advertises a new method for fraud, perhaps it would be time to test your own system for vulnerabilities and prevent any victimization. Our suggestion is therefore that Canadian Financial Institutions pay close attention not only to the threats against themselves but also to the threats against the Canadian financial industry as precious information could help them secure their own infrastructure.
Flare Systems is a threat intelligence solution providing immediate actionable data about threats and actors to financial institutions from the Dark Web, cyber criminal communities and monitored conversations. Learn more about us on our web page or by contacting us.
Subscribe to our blog to stay up to date on darknet and cybersecurity.
Related articles