Everyday, Flare Systems collects leaked usernames and passwords on the internet and the darkweb. Our customers use our extensive leaked credentials database to prevent credential stuffing attacks.
Credential stuffing happens when malicious actors take a database of leaked usernames and passwords and test these credentials on a different website. If the victims reused the same email and password combination on multiple sites, malicious actors can take over their accounts or resell the credentials.
Instead of analyzing passwords ‘normal‘ people and offenders use, as we have done in the past, we explore below the risks of employees using their corporate emails to register for personal accounts on external websites.
Our investigation shows that credentials associated with a corporate email can be used to improve cracking attacks that put your company at risk, hurt your firms’ reputation and even leak sensitive information. We recommend that your policies forbid your employees using corporate email addresses when registering for personal accounts and make them aware of the risks of using corporate emails for personal reasons.
Use of corporate email addresses
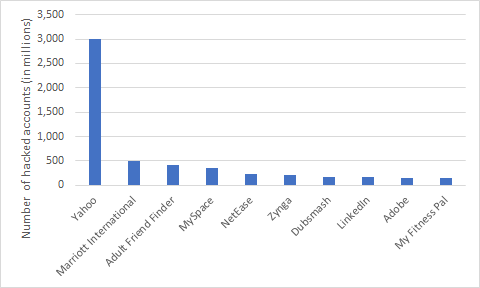
Most credentials leaks come from hacked databases. The figure below presents the biggest leaks of the past decade. We commonly find corporate emails as usernames in many of those leaks. This is not surprising given the business customer base of the hacked companies (ex. Marriott International, Adobe).
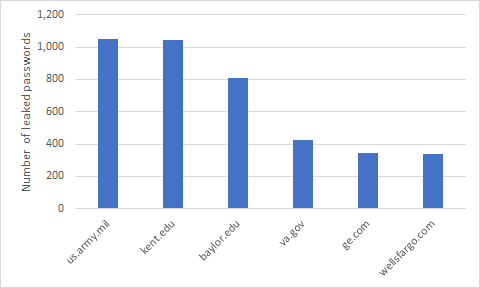
However, it is surprising to find corporate emails in the leaks for MyFitnessPal. What business reason would there be to register on those services with a corporate email? Analysis shows that most common corporate domain names found in the MyFitnessPal leak belonged to a broad range of industry sectors such as military, education, and financial services. Take a look at the figure below to see the top 6 domains in MyFitnessPal leaked credentials.
So why should you and your company monitor for leaked passwords for your corporate email addresses?
Leaks can be used to better profile passwords
There are many similarities between the top passwords in different industries and companies. Employees in an industry or a specific company are likely to follow specific patterns in how they choose passwords. Malicious actors use those patterns to make better educated guesses of what password a user is likely to use. If successful in guessing the password, malicious actors can take over an account and even gain remote access to a computer, a hazard that has become more serious in the light of the current situation of remote workforce.
Using the leaked passwords from MyFitnessPal, we analyzed the passwords of 13 security-focused entities and present a list of their 10 most common passwords.
- 1234
- 123456
- testing
- password
- stratfor
- johnlock
- police
- waterart
- summer
- fitness
123456 is a common password for pretty much everyone, including members of security-focused entities and everyone else. However, new passwords such as police and stratfor (an infamous private security company) also appear in this list.
We also observed that passwords of these entities contain on average:
- 71% of lowercase characters
- 24% of digits
- 5% of uppercase characters and special characters
Malicious actors feed these statistics into their cracking tools and can significantly improve their success rate.
Other risks
Most leaked passwords are innocuous or will make you smile, even. Some, however, can surprise you or tarnish a firms’ reputation because they contain illicit drug names or not appropriate (NSFW) words. Passwords can also leak personal information such as birthdays, telephone numbers and even home addresses. Over a quarter of all leaked passwords analyzed in a 2017 study found that they contained the aforementioned personal information.
Main takeaways
It is quickly becoming a common practice for companies to protect themselves by subscribing to feeds of leaked credentials. They can then compare the leaked passwords against those of their employees and customers and refuse connections that reuse leaked credentials.
Leaked credentials represent a significant potential threat beyond the simple reuse of passwords. Proactive actions should be taken by organizations to protect against these threats.
To mitigate these risks, we invite organizations to:
- Proactively monitor for leaked credentials using a monitoring product and put in place a policy for a password change as soon as a corporate email address is discovered to be among a leak.
- Provide their employees with a password manager service that generates new and random passwords each time they register an account.
- Offer awareness training for their employees about the risks of using corporate emails for external personal accounts.
- Analyze the patterns of their leaked passwords and compare them to the passwords of their employees and customers. Any password that matches those patterns should be replaced.
- Invite employees to change their passwords that contain personal identifiable information.
Most importantly, however, companies should enforce a policy to limit the use of corporate emails to signup for services not deemed necessary for business purposes. This remains the best security solution.
To learn more about Flare System’s password leak protection system, request your demo today.