Flare’s Threat Exposure Management solution integrates into your security program in 30 minutes to provide your team with actionable intelligence and automated remediation for threats across the clear & dark web.







Check out our case studies to see real life examples of how security teams use Flare to reduce risk.
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data.”
“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth.“
“Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5-point scoring system.”
“Flare enables us to react quickly when threats are publicized. It helps us protect our brand and financial resources from data breaches.”
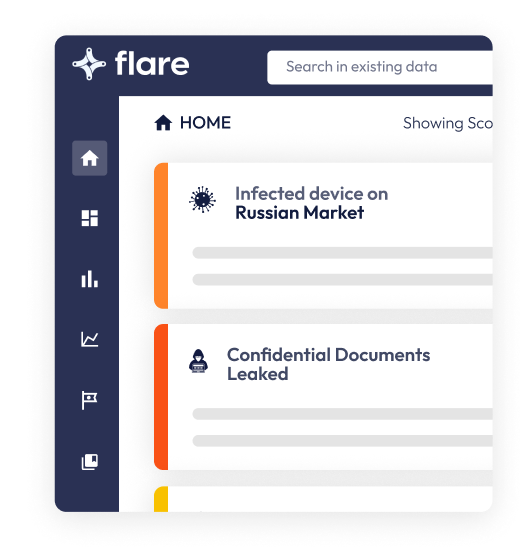
Flare unifies monitoring of thousands of cybercrime communities & clear web sites to proactively detect the threats that lead to ransomware attacks, data breaches, and security incidents.

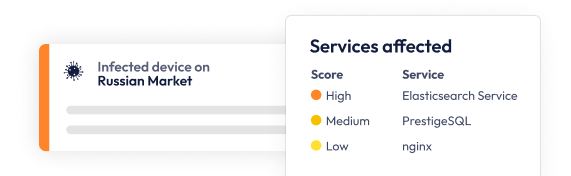
We’ve tailored Flare’s coverage to provide high-fidelity, actionable intelligence that is specific to your organization. We focus on maximizing relevant context while minimizing unnecessary alerts, leading to less wasted SOC time, faster time to detection, and reduced risk.
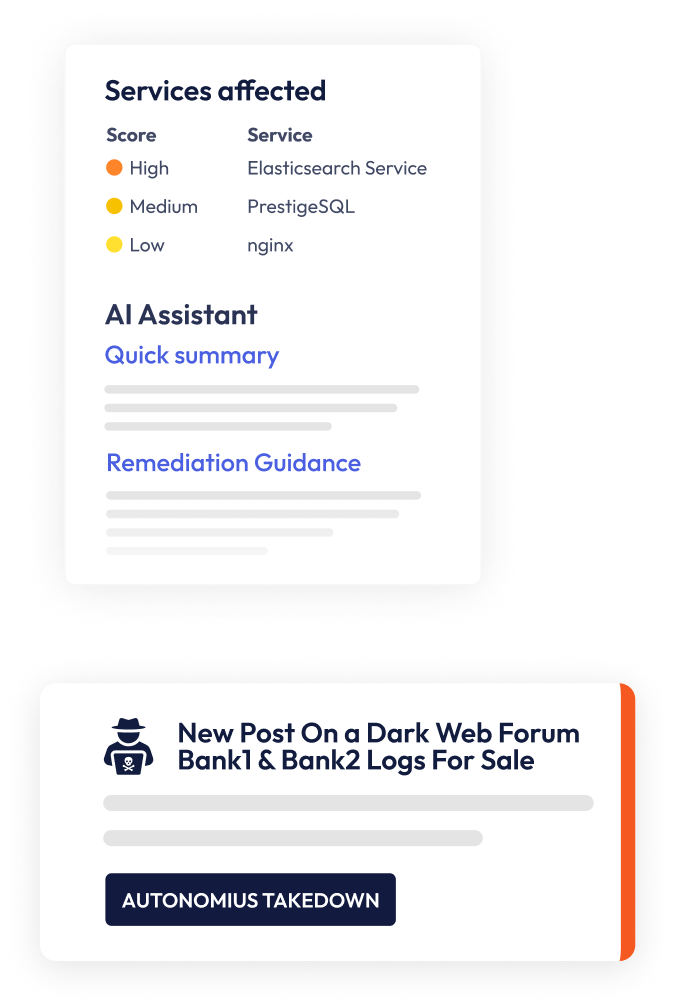
At Flare, we’ve focused on building a platform that enables end to end collection to remediation. Using AI language models, we can autonomously takedown lookalike domains and public GitHub secrets disclosure at the click of a button.

Flare collects intelligence from across the clear & dark web. Our collection rivals or eclipses legacy CTI providers while providing:

Flare AI can take inputs from any language on earth and deliver actionable intelligence at scale. Flare AI Assist seamlessly translates Russian, Arabic, Spanish, French, and other threat actor forum posts into seamless English summaries that provide rich context.
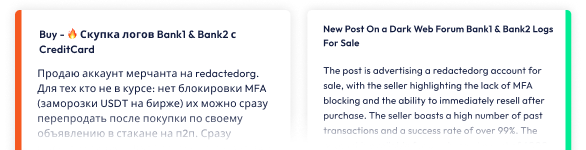


Simple, Effective Monitoring for Dark Web Forums, Markets, Infected Device Marketplaces, and thousands of Illicit communities across the clear & dark web.
Proactively detect leaked secrets from public GitHub repositories, paste sites, and other public forums.
Get unified visibility into open ports, data leaks, and threat actors selling your information across the clear & dark web.
The average Flare customer is set up and running in 30 minutes with our easy to use dark web monitoring platform.
We’ve built native integrations with leading SIEM, SOAR, and ticketing solutions along with a robust REST API that enables you to seamlessly integrate Flare’s threat exposure data into different security functions.
Check out our case studies to see real life examples of how security teams use Flare to reduce risk.
See how one of North Americas top investment firms used Flare’s platform to prevent a major portfolio company breach.
See how one of North America’s largest banks streamlined sensitive data leak monitoring. They were able to cut incident response costs by 95%.
A North American managed security service provider (MSSP) unlocked new revenue streams and reduced dark web investigation time by 10x.

Flare’s Resource Center is your definitive source for all things about Flare’s platform for external threat management and risk protection.
Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune 50, financial institutions, and software startups.
